
Agent-Based Digital Identity Architecture
Problems — Analysis — Solution — Adoption
Problems Plaguing the Web
Today’s web is a provider-centered patchwork of schemes incapable of ubiquitously distinguishing impersonators from reliable sources. Public Key Infrastructure (PKI) has reliably secured Internet services for decades. But identity, privacy, and ease-of-use for ordinary users have been neglected. Biometric authenticators and second factors have strengthened user-to-provider bindings. But reliable methods for users to present their digital identities when needed are not available. Financial, government and defense sector organizations have instituted various (non-standard) procedures for identity-proofing users and issuing credentials to authenticate them. However, social networks and other providers gather little or no evidence validating user-asserted identifying information. Self-asserting identity does not prove who you are. Meanwhile, users and providers are frustrated maintaining countless passwords, resetting them, and keeping online profiles current. Passwords are often weakly specified and routinely reused across multiple services. And users are obliged to cope with much span and potentially harmful scams. Unsurprisingly, impersonators, hackers and fraudsters continue to exploit these deficiencies.
Analysis
Judiciously decentralizing control over identity from service providers to users benefits them both. Using proven cryptographic methods (elliptic curve, ephemeral keys, Diffie-Hellman) overcomes weaknesses and frustrations associated with having so many remote access passwords and online user profiles to manage. Reliance on passwords can be significantly reduced by provisioning intutitive, easy-to-use digital identities enabling users and providers to mutually identify, mutually authenticate, and mutually secure their transactions. Cryptographically-enabled digital identities can be safely used across multiple providers in many cases. Strategic application of biometrics, cryptography, and identity-proofing elevates identity assurances and authentication assurances benefiting users and providers alike.
Solution: Better than your Wallet
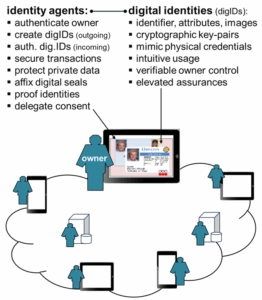
Technology Adoption
A progressive approach anchored by a focused initial project is planned. To facilitate technology adoption, usability, privacy, security, and ubiquity have been baked into the solution. A proof-of-concept prototype has been developed to validate the architecture. Working in the best interests of users and providers, identity agents create inutitive digital identities having the look and feel of physical credentials in one’s wallet facilitating ease-of-use. Digital identities are verifiably owner-controlled (self-sovereign). Users and providers create digital seals cryptographically binding them to their digital identities; to the digital identities of others; to documents; and to delegated consent tokens. These capabilities enable users and providers to create, exchange, and use digital identities to mutually identify, authenticate, collaborate, and protect their identifying and private information.
Possible Application of AI
Going forward, identity agents will be able to exploit artificial intelliegence (AI) to prevent impersonation, phishing, and man-in-the-middle (MITM) attacks. They will optimize decision-making for owners by assessing which digital identities to use and how much private information to disclose in a given circumstance.